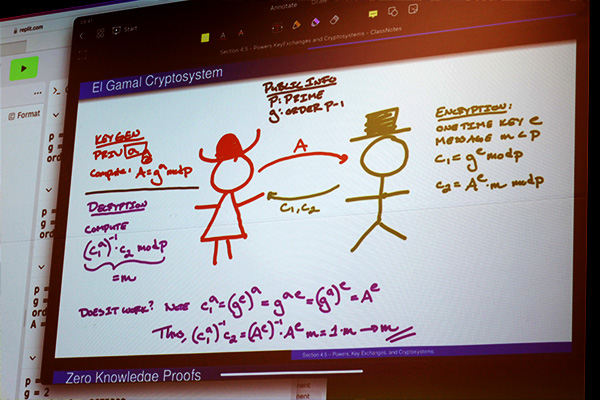
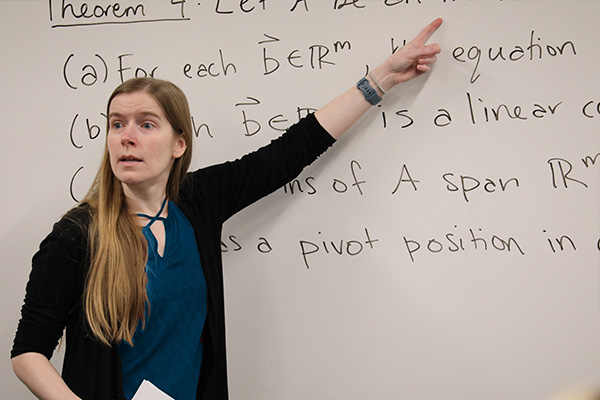Explore Programs
Discover, explore, and succeed in a field you love
After you've checked out our programs, be sure to head over to our Admissions page, where you'll find information on how to apply to DSU, sign up for a visit, or preview your program.